Dynamically configure YARA rules in Veeam
Disclaimer:
I’m not a professional developer. This guide is intended to demonstrate the “art of the possible” rather than serve as production-ready code. Use this example with caution, and always test thoroughly in your environment before relying on it for critical tasks. Auto-Yara
Introduction
With the rise of cyberattacks becoming more and more prevalent each day, the need to perform proactive threat hunting is becoming increasingly essential for organizations of all sizes. One powerful tool in a threat hunter’s arsenal is YARA—a tool used to identify and classify malware by creating rules based on textual or binary patterns. YARA is widely adopted across the cybersecurity industry due to its flexibility and precision in detecting both known and novel threats.
In the context of Veeam, YARA plays a crucial role in enhancing cybersecurity posture. By integrating YARA rule scanning into Veeam environments, security teams can proactively scan backed-up data for indicators of compromise (IOCs), ensuring threats are detected even in dormant or historical datasets. This capability transforms Veeam from a traditional backup solution into a powerful security ally.
In this post, we’ll explore how to dynamically configure YARA rules in Veeam, enabling more responsive and adaptable threat detection. Whether you’re a security analyst or a systems administrator, this guide will walk you through the process step-by-step so you can strengthen your defenses with confidence.
The Process at a Glance
I just wanted to give a shout out to ransomware.live who helped make this possible, I was struggling to find a good source of Yara rules broken down by threat actors and found this to be the most comphrensive however I needed to be able to pull this info via an API, I emailed them and requested the API endpoint be added and they happily added it which is just amazing so please go visit their site, buy them a coffee if you wish, they are amazing and have a wealth of information.
This process works by automatically retrieving the latest YARA rule files from ransomware.live and placing them in the appropriate directory within the Veeam environment. Veeam then detects these new rules dynamically—without the need to restart any services or even close the console—making them immediately available for use.
Ideally, this task should be scheduled to run on a daily or weekly basis, depending on your security team’s requirements. Once in place, you can begin proactively scanning your existing backups and performing ongoing threat hunting with minimal manual effort.
-
Configure the Automation Script Set up the script within your Veeam environment to download and manage YARA rule updates.
-
Verify YARA Rule Sync Ensure the rules are being successfully retrieved and placed in the correct Veeam directory.
-
Open the Veeam Console No need to restart—Veeam will automatically detect the new rules.
-
Perform Threat Hunting Scans Use the freshly updated YARA rules to scan your backups for indicators of compromise directly from the console.
Once everything is in order and has been configured correctly you should see the below.
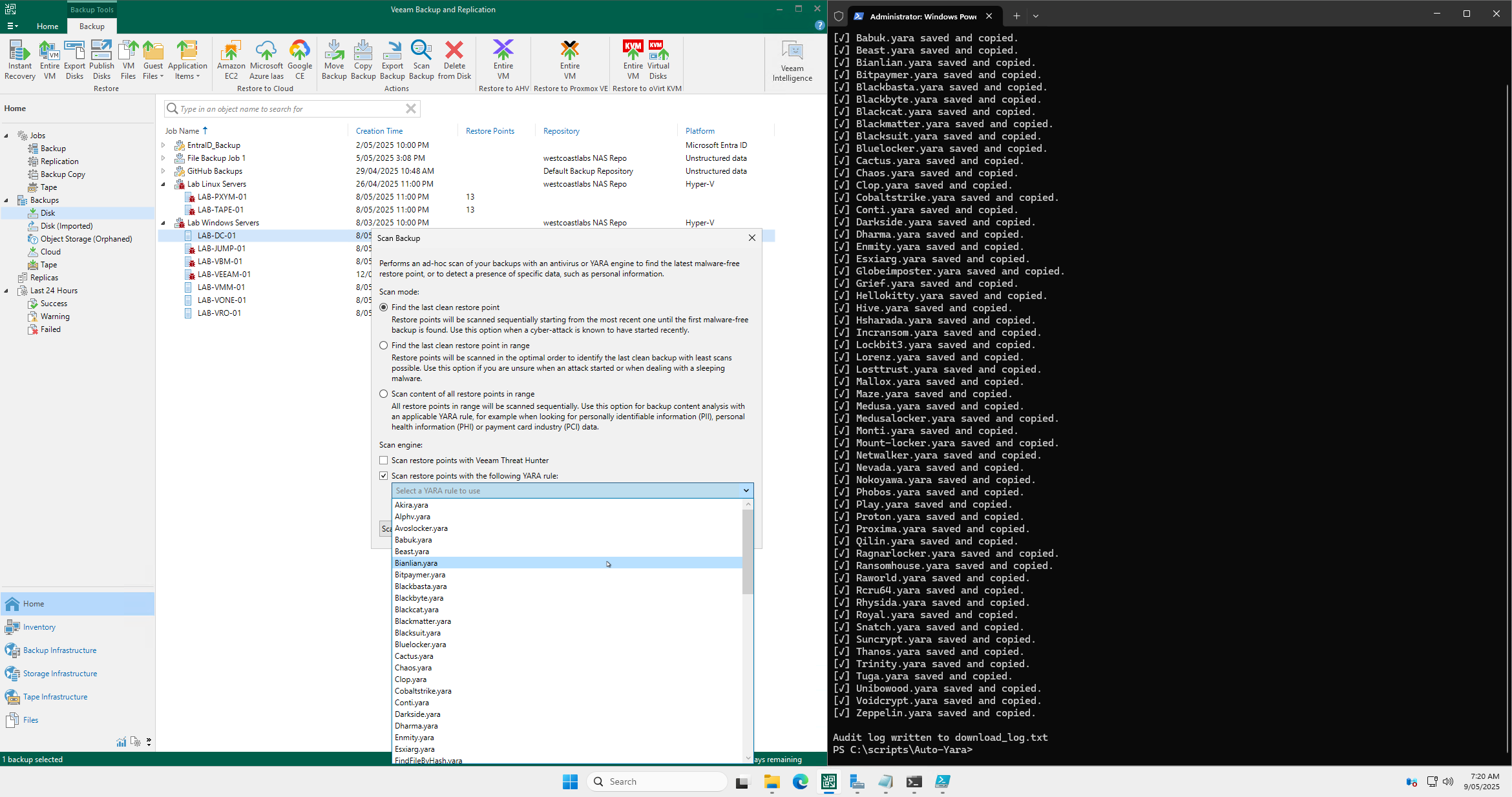
The true power of this approach lies in its flexibility—you can use any YARA rules available to you, whether they’re provided by a security vendor, written in-house, or sourced from the broader cybersecurity community. This opens the door to virtually limitless possibilities for threat detection and reinforces the value of Veeam as not just a backup solution, but a versatile and adaptable security platform.
Conclusion
As cyber threats continue to evolve, it’s critical for organizations to go beyond traditional backup strategies and adopt proactive security measures. By integrating YARA with Veeam and dynamically configuring your rules, you gain the ability to detect threats hiding within backup data—before they can cause damage during a restore or compromise other systems.
This approach not only enhances your incident response capabilities but also turns your backup infrastructure into an additional layer of defense. With the steps outlined above, you can begin building a more resilient and intelligent data protection strategy that aligns with today’s threat landscape.
Thanks for reading—I hope you found this guide helpful. As always, stay curious and keep learning!