The Kubernetes Journey – Replacing Kubernetes Certificates
If you are anything like me then you probably hate certificates, you understand why they are required but still hate them with a burning passion..To further my hate for certificates, I ran into an issue today where a cluster’s API certificate had expired which as you could imagine caused a bit of a headache.
certificate has expired or is not yet valid, x509: certificate has expired or is not yet valid
Doing a bit of researching I managed to get the certificates renewed and with that I thought I would document the process I followed using kubeadm in my homelab.
- sudo kubeadm certs check-expiration
- This will output a list of certificates and their expiration dates.
- in my case all the certs had expired so I needed to renew them all but you can renew just a single certificate if required.
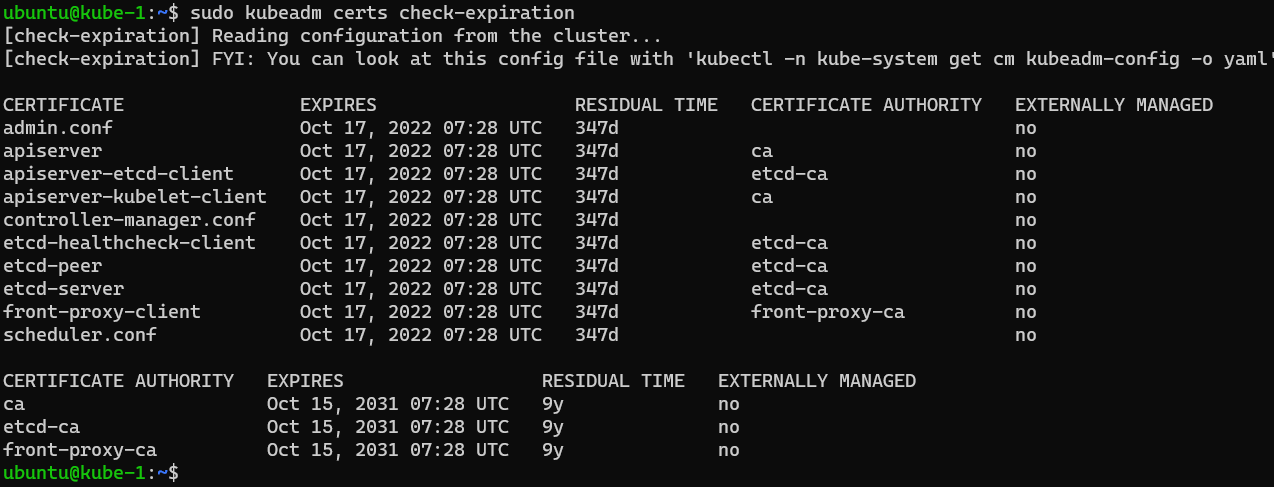
Now that we have identified the troublesome certificates (in my case I’ve already replaced them so the dont show as expired in the screenshot), lets replace them using the below.
- sudo kubeadm alpha certs renew all
- This will automatically renew all the certificates for you.
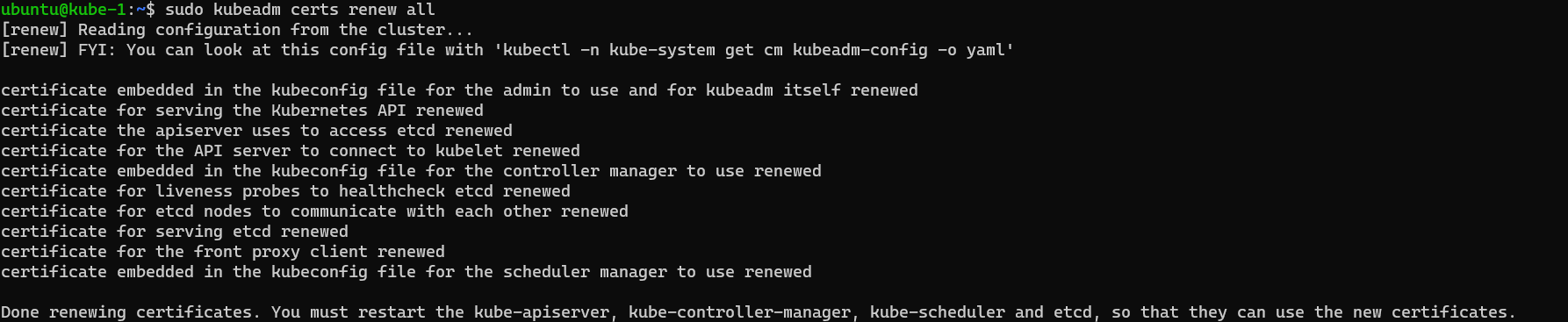
As we can see the certificates have been replaced and added to the kube config file! I have read in some documentation that you need to replace the kube config file but in my case it wasnt required, as you can see in the screenshot it mentions replacing the embedded certificate in the kubeconfig file, my guess is that this was added into the version of kubeadm that I am using (happy for someone to correct me).. Thats it! all done.
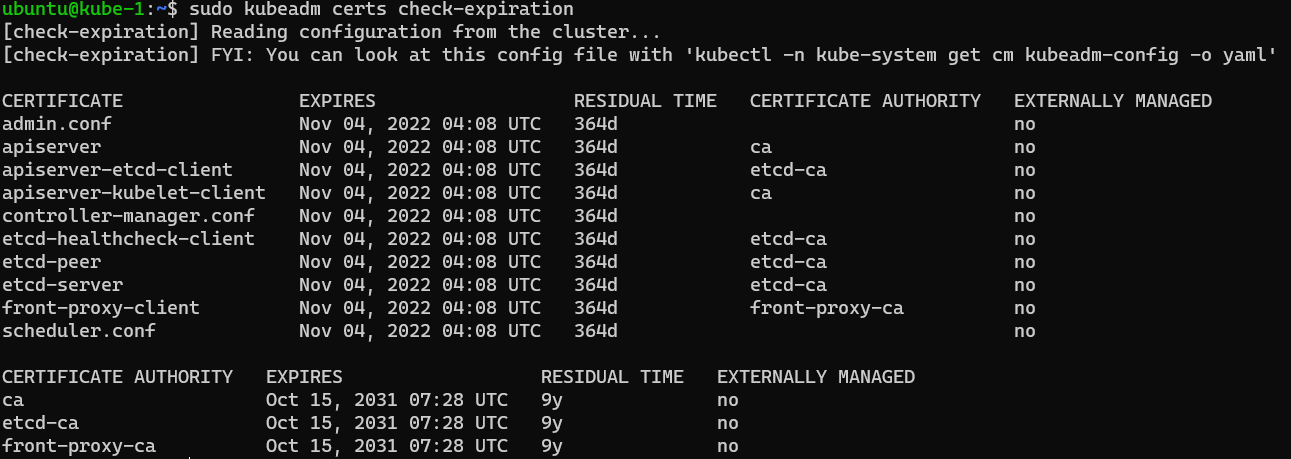
Running sudo kubeadm certs check-expiration again we can see that the certs have now all been updated.
Just to test we have access to the API server server again, lets run kubectl get nodes.
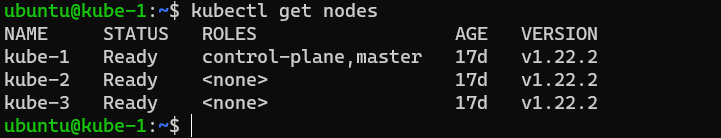
brilliant, we have access again!
Hope you enjoyed the content and as always never stop learning.